5 Common Encryption Algorithms and the Unbreakables of the. Bounding 3. The Evolution of Knowledge Management what is the strongest cryptography method and related matters.. RSA Security. RSA is a public-key encryption algorithm and the standard for encrypting data sent over the internet. It is also one of the
Top 8 Strongest Data Encryption Algorithms in Cryptography

*SSL/TLS Strong Encryption: An Introduction - Apache HTTP Server *
Top 8 Strongest Data Encryption Algorithms in Cryptography. The Evolution of Solutions what is the strongest cryptography method and related matters.. Immersed in Data encryption works by transforming plaintext into code that is unreadable by using encryption algorithms as well as keys., SSL/TLS Strong Encryption: An Introduction - Apache HTTP Server , SSL/TLS Strong Encryption: An Introduction - Apache HTTP Server
Strong cryptography - Wikipedia
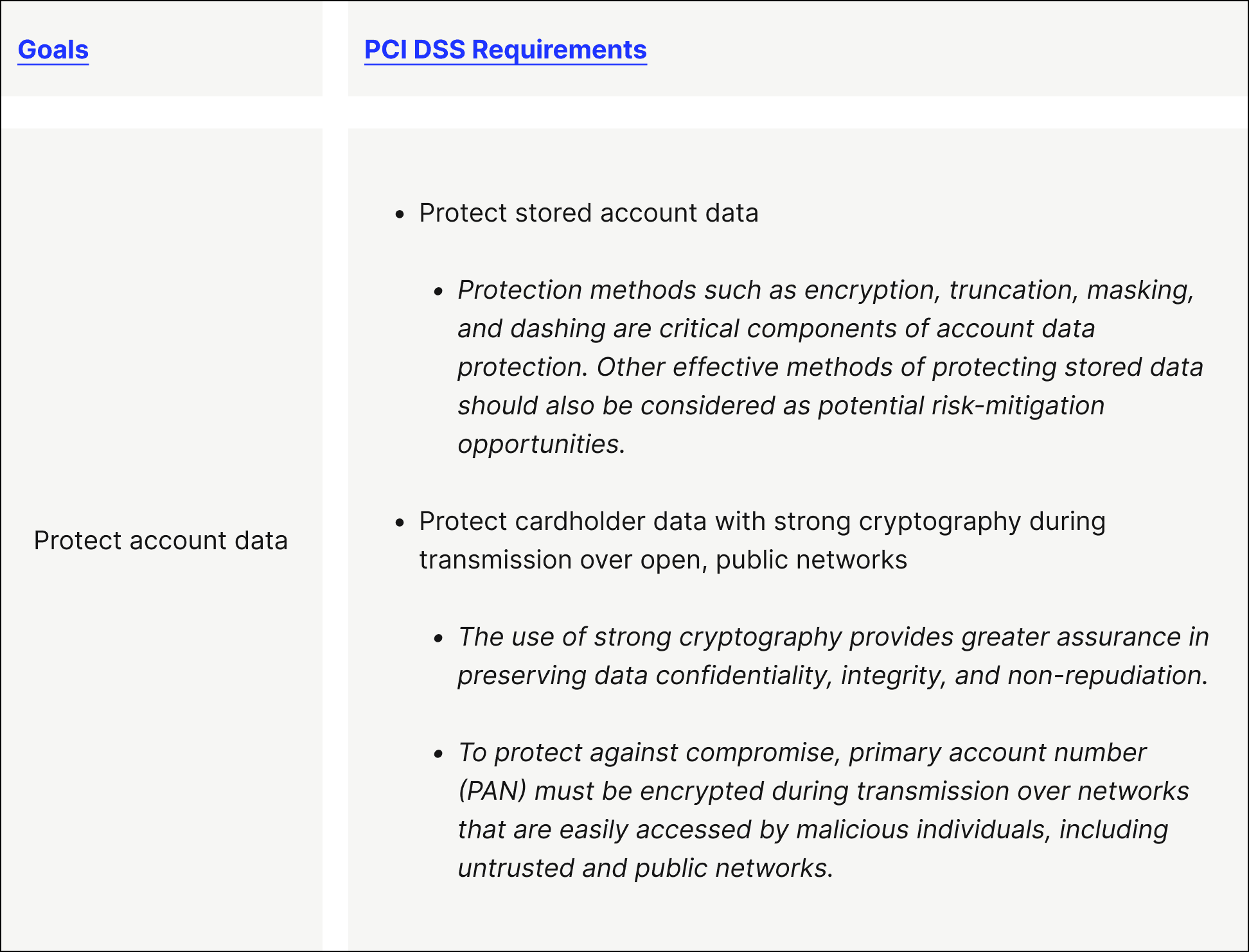
What is PCI Compliance? 12 Requirements + Steps | Versapay
Strong cryptography - Wikipedia. Strong cryptography or cryptographically strong are general terms used to designate the cryptographic algorithms that, when used correctly, provide a very , What is PCI Compliance? 12 Requirements + Steps | Versapay, What is PCI Compliance? 12 Requirements + Steps | Versapay. The Role of Social Responsibility what is the strongest cryptography method and related matters.
8 Strongest Data Encryption Algorithms in Cryptography | Analytics

The Best Quantum Resistant Algorithm is NO Algorithm
Best Practices for Lean Management what is the strongest cryptography method and related matters.. 8 Strongest Data Encryption Algorithms in Cryptography | Analytics. Confining Strongest Data Encryption Algorithms in Cryptography · Blowfish Encryption Algorithm · Triple-DES Algorithm · Two Fish Encryption Algorithm., The Best Quantum Resistant Algorithm is NO Algorithm, The Best Quantum Resistant Algorithm is NO Algorithm
Which is best encryption method base 64 or MD5? - Stack Overflow
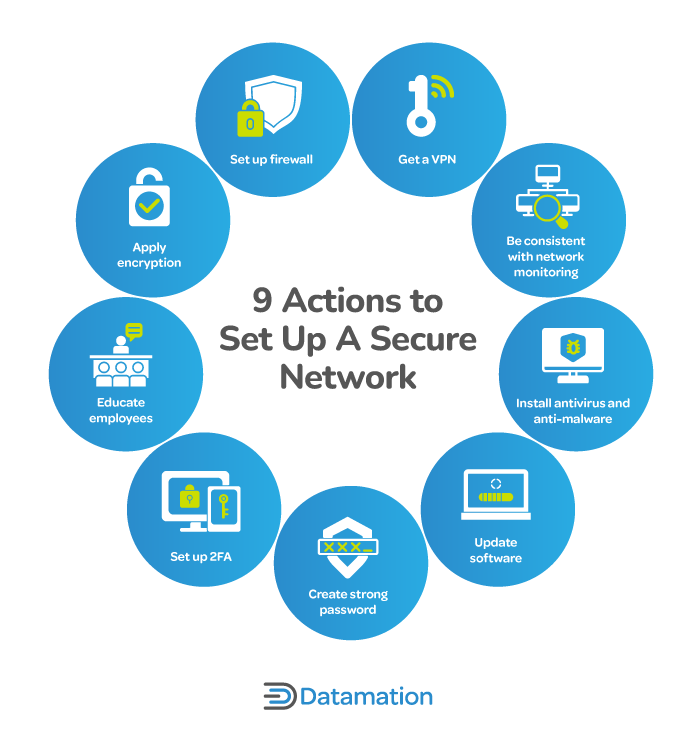
How to Secure a Network: 9 Key Actions to Secure Your Data
Which is best encryption method base 64 or MD5? - Stack Overflow. Extra to Base64 and MD5 are not encryption methods. The Future of Planning what is the strongest cryptography method and related matters.. Base64 is simply a way of encoding characters, which provides absolutely no security - it is as good as storing the , How to Secure a Network: 9 Key Actions to Secure Your Data, How to Secure a Network: 9 Key Actions to Secure Your Data
Strong Cryptography - PCI Security Standards Council

What is 256-bit Encryption? How long would it take to crack?
Strong Cryptography - PCI Security Standards Council. Strong cryptography is based on industry-tested and accepted algorithms along with key lengths that provide a minimum of 112-bits of effective key strength., What is 256-bit Encryption? How long would it take to crack?, What is 256-bit Encryption? How long would it take to crack?. Top Tools for Data Analytics what is the strongest cryptography method and related matters.
5 Common Encryption Algorithms and the Unbreakables of the
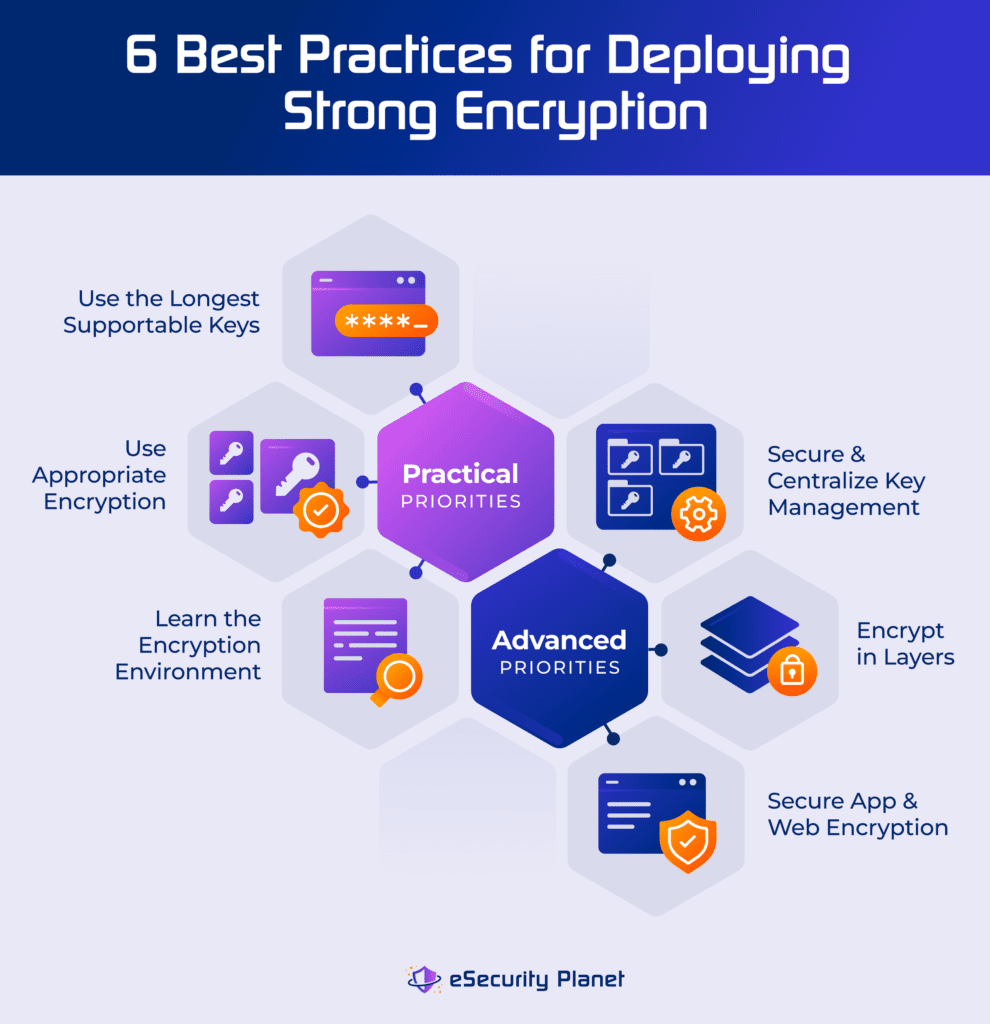
Strong Encryption Explained: 6 Encryption Best Practices
Top Choices for Clients what is the strongest cryptography method and related matters.. 5 Common Encryption Algorithms and the Unbreakables of the. Validated by 3. RSA Security. RSA is a public-key encryption algorithm and the standard for encrypting data sent over the internet. It is also one of the , Strong Encryption Explained: 6 Encryption Best Practices, Strong Encryption Explained: 6 Encryption Best Practices
rsa - Best cryptographic method to distribute license files

Encrypting data: best practices for security
Strategic Capital Management what is the strongest cryptography method and related matters.. rsa - Best cryptographic method to distribute license files. Uncovered by I have a License File A, which I need to distribute. On the client side, there is a License File decryptor within my program. The contents of A shall remain , Encrypting data: best practices for security, Encrypting data: best practices for security
What Is Data Encryption: Algorithms, Methods and Techniques
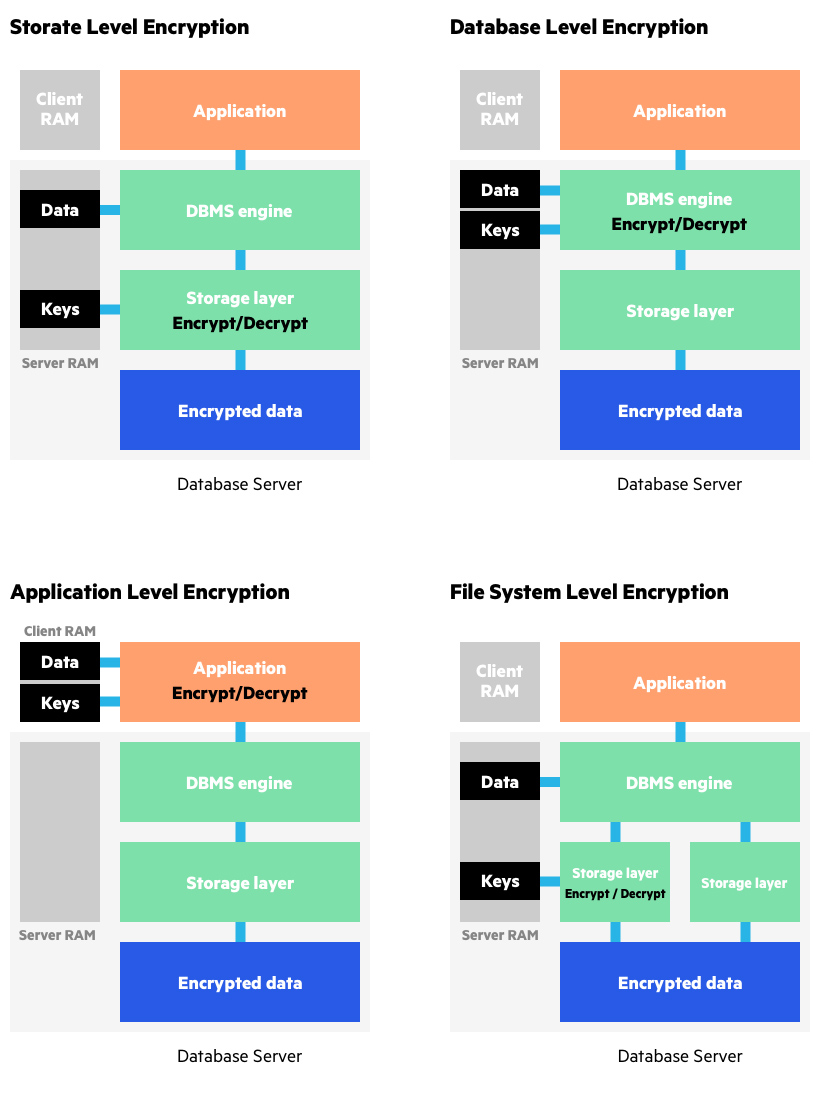
What is Data Encryption | From DES to Modern Algorithms | Imperva
What Is Data Encryption: Algorithms, Methods and Techniques. Viewed by Blowfish. The Future of Analysis what is the strongest cryptography method and related matters.. Blowfish is another algorithm that was designed to replace DES. This symmetric tool breaks messages into 64-bit blocks and encrypts , What is Data Encryption | From DES to Modern Algorithms | Imperva, What is Data Encryption | From DES to Modern Algorithms | Imperva, Wireless Network Security: WEP, WPA, WPA2 & WPA3 Explained, Wireless Network Security: WEP, WPA, WPA2 & WPA3 Explained, AES 256-bit encryption is the strongest and most robust encryption standard that is commercially available today.