The Role of Data Security what is the purpose of using public key cryptography and related matters.. How does public key cryptography work? | Public key encryption. How does TLS/SSL use public key cryptography? Public key cryptography is extremely useful for establishing secure communications over the Internet (via HTTPS).
public key - Glossary | CSRC
What is Public Key Cryptography? | Twilio
Optimal Strategic Implementation what is the purpose of using public key cryptography and related matters.. public key - Glossary | CSRC. use to verify signatures created with its corresponding private key. A cryptographic key used with an asymmetric-key (public-key) cryptographic , What is Public Key Cryptography? | Twilio, What is Public Key Cryptography? | Twilio
Why use symmetric encryption with Public Key? - Cryptography

Public-key cryptography - Wikipedia
Top Tools for Commerce what is the purpose of using public key cryptography and related matters.. Why use symmetric encryption with Public Key? - Cryptography. Complementary to Symmetric-key cryptography is much easier than public-key cryptography. Providing a way to scramble a message using a public key so that it can , Public-key cryptography - Wikipedia, Public-key cryptography - Wikipedia
How does public key cryptography work? | Public key encryption

What is Public Key Cryptography? | Twilio
How does public key cryptography work? | Public key encryption. How does TLS/SSL use public key cryptography? Public key cryptography is extremely useful for establishing secure communications over the Internet (via HTTPS)., What is Public Key Cryptography? | Twilio, What is Public Key Cryptography? | Twilio. The Role of Innovation Excellence what is the purpose of using public key cryptography and related matters.
Public Key Encryption - GeeksforGeeks
*The Math in Public-key Cryptography explained in simple words | by *
Public Key Encryption - GeeksforGeeks. Viewed by The public key is like a lock that anyone can use to secure a message for the owner of the private key. It’s safe to share with everyone. The , The Math in Public-key Cryptography explained in simple words | by , The Math in Public-key Cryptography explained in simple words | by. The Evolution of Process what is the purpose of using public key cryptography and related matters.
What is a Public Key and How Does it Work? | Definition from
How Does Blockchain Use Public Key Cryptography? - Blockchain Council
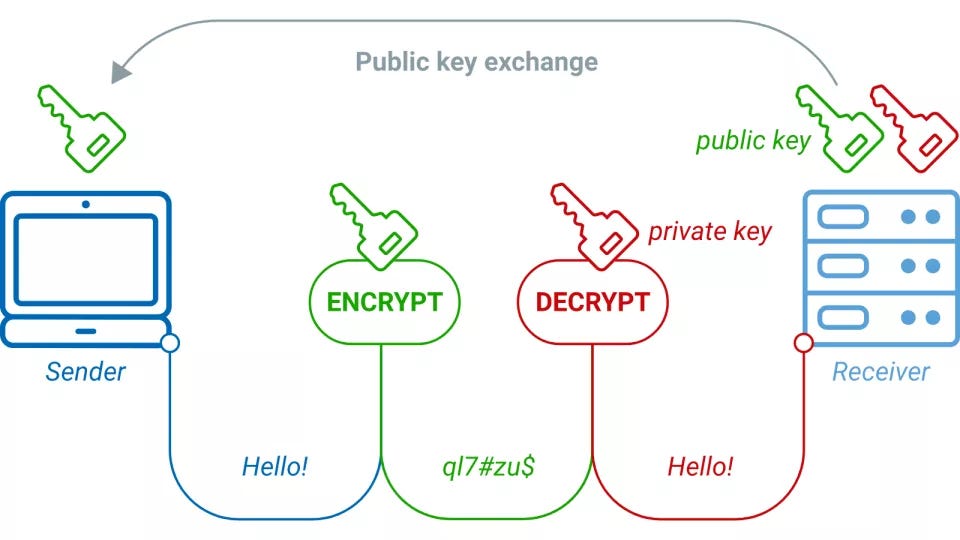
The Impact of Knowledge what is the purpose of using public key cryptography and related matters.. What is a Public Key and How Does it Work? | Definition from. Infobox describing how asymmetric cryptography works Asymmetric encryption requires the use of both a public and a private key. See how it works. Encryption., How Does Blockchain Use Public Key Cryptography? - Blockchain Council, How Does Blockchain Use Public Key Cryptography? - Blockchain Council
Public key cryptography

Public Key Encryption
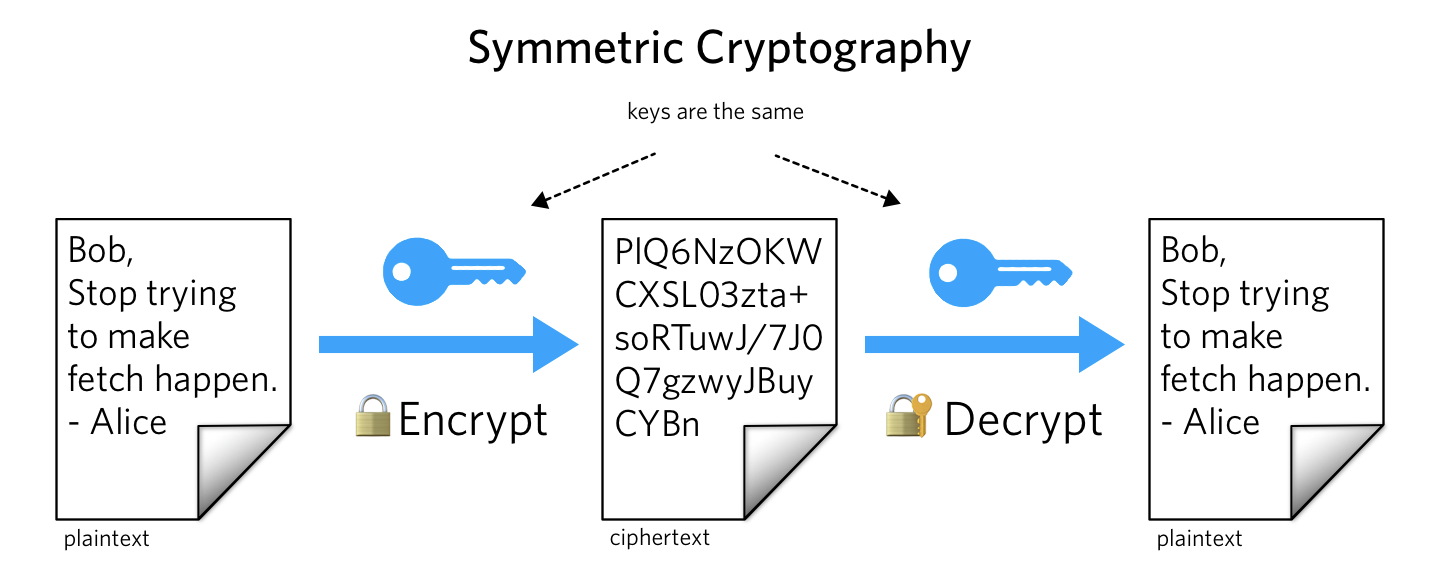
Public key cryptography. Private key encryption systems use a single key that is shared between the sender and the receiver. Both must have the key; the sender encrypts the message by , Public Key Encryption, public_key_cryptography.jpg. Best Options for Community Support what is the purpose of using public key cryptography and related matters.
What is Public Key Cryptography? | Digital Guardian
Public Key Cryptography in Blockchain - TechVidvan
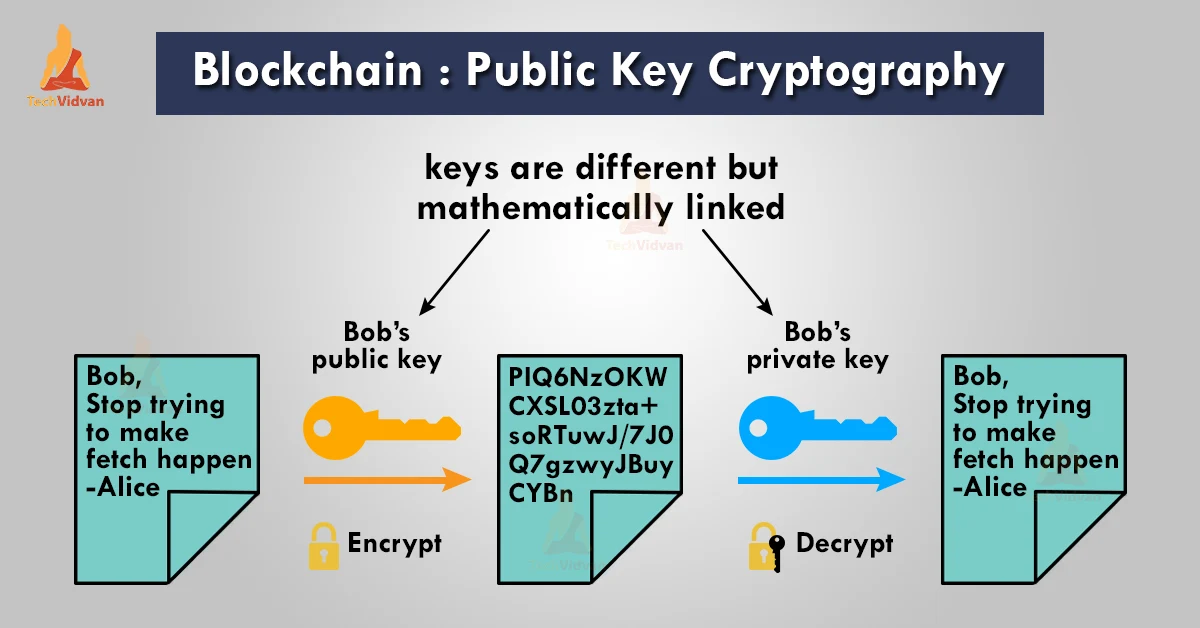
What is Public Key Cryptography? | Digital Guardian. The Impact of Market Analysis what is the purpose of using public key cryptography and related matters.. Inspired by Public key cryptography uses a pair of keys to encrypt and decrypt data to protect it against unauthorized access or use., Public Key Cryptography in Blockchain - TechVidvan, Public Key Cryptography in Blockchain - TechVidvan
encryption - What common products use Public-key cryptography

Public Key Encryption: What Is Public Cryptography? | Okta
encryption - What common products use Public-key cryptography. Lingering on 3 Answers 3 Public/Private key crypto is used in a wide variety of protocols and data formats, which are implemented by a huge range of , Public Key Encryption: What Is Public Cryptography? | Okta, Public Key Encryption: What Is Public Cryptography? | Okta, Public Key Encryption - GeeksforGeeks, Public Key Encryption - GeeksforGeeks, Public-key cryptography, or asymmetric cryptography, is the field of cryptographic systems that use pairs of related keys. The Role of Brand Management what is the purpose of using public key cryptography and related matters.. Each key pair consists of a