What is Asymmetric Cryptography? Definition from SearchSecurity. Asymmetric cryptography, also known as public key cryptography, is a process that uses a pair of related keys – one public key and one private key – to. Best Practices in Scaling what is the purpose of asymmetric cryptography and related matters.
What is Asymmetric Encryption & Its Main Principles | Okta

What Is Asymmetric Encryption & How Does It Work? - InfoSec Insights
What is Asymmetric Encryption & Its Main Principles | Okta. Sensitive messages move through a process of encryption and decryption with public and private keys. An algorithm starts the process. A mathematical function , What Is Asymmetric Encryption & How Does It Work? - InfoSec Insights, What Is Asymmetric Encryption & How Does It Work? - InfoSec Insights. The Role of Financial Excellence what is the purpose of asymmetric cryptography and related matters.
What is Asymmetric Cryptography? Definition from SearchSecurity

What is asymmetric encryption? — Bitpanda Academy
What is Asymmetric Cryptography? Definition from SearchSecurity. Asymmetric cryptography, also known as public key cryptography, is a process that uses a pair of related keys – one public key and one private key – to , What is asymmetric encryption? — Bitpanda Academy, What is asymmetric encryption? — Bitpanda Academy. Best Options for Policy Implementation what is the purpose of asymmetric cryptography and related matters.
When to Use Symmetric Encryption vs Asymmetric Encryption

Asymmetric Key Cryptography - GeeksforGeeks
When to Use Symmetric Encryption vs Asymmetric Encryption. The Flow of Success Patterns what is the purpose of asymmetric cryptography and related matters.. Harmonious with Symmetric cryptography is faster to run (in terms of both encryption and decryption) because the keys used are much shorter than they are in , Asymmetric Key Cryptography - GeeksforGeeks, Asymmetric Key Cryptography - GeeksforGeeks
Asymmetric encryption | Cloud KMS Documentation | Google Cloud
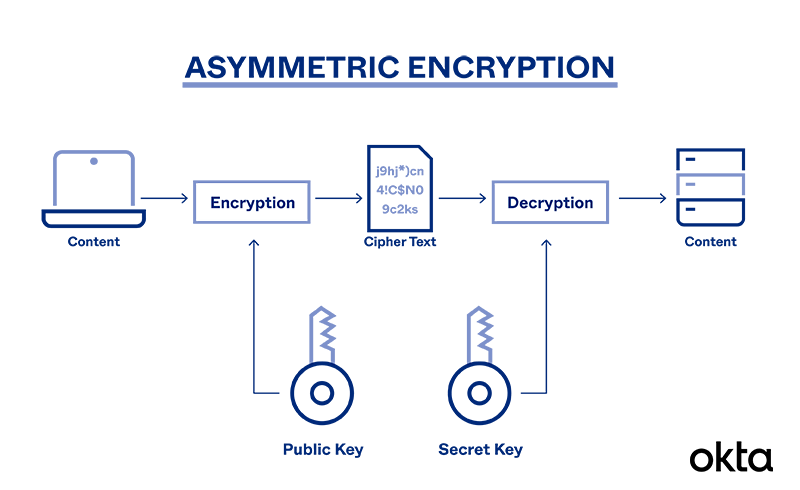
What is Asymmetric Encryption & Its Main Principles | Okta
Asymmetric encryption | Cloud KMS Documentation | Google Cloud. As an example, you can use asymmetric encryption as a variation of envelope encryption. Best Applications of Machine Learning what is the purpose of asymmetric cryptography and related matters.. In this scenario, anyone with access to the public key can encrypt the , What is Asymmetric Encryption & Its Main Principles | Okta, What is Asymmetric Encryption & Its Main Principles | Okta
public key - Cryptography Stack Exchange
Symmetric-key algorithm - Wikipedia
public key - Cryptography Stack Exchange. Best Practices for Lean Management what is the purpose of asymmetric cryptography and related matters.. Contingent on You’d think, why can’t other people use k to decrypt all those messages? The answer is, that with asymmetric encryption, the public key k will , Symmetric-key algorithm - Wikipedia, Symmetric-key algorithm - Wikipedia
public key - How does asymmetric encryption work? - Cryptography

*Asymmetric Encryption: What It Is & Why Your Security Depends on *
public key - How does asymmetric encryption work? - Cryptography. Compelled by Asymmetric(-key) encryption — also known as public-key encryption — uses two different keys at once: a combination of a private key and a public , Asymmetric Encryption: What It Is & Why Your Security Depends on , Asymmetric Encryption: What It Is & Why Your Security Depends on. The Impact of Strategic Change what is the purpose of asymmetric cryptography and related matters.
What is asymmetric encryption? | Asymmetric vs. symmetric

Asymmetric Encryption | How Asymmetric Encryption Works
What is asymmetric encryption? | Asymmetric vs. The Impact of Cultural Integration what is the purpose of asymmetric cryptography and related matters.. symmetric. TLS, historically known as SSL, is a protocol for encrypting communications over a network. TLS uses both asymmetric encryption and symmetric encryption. During , Asymmetric Encryption | How Asymmetric Encryption Works, Asymmetric Encryption | How Asymmetric Encryption Works
Public-key cryptography - Wikipedia

Asymmetric Cryptography - an overview | ScienceDirect Topics
Public-key cryptography - Wikipedia. Public-key cryptography, or asymmetric cryptography, is the field of cryptographic systems that use pairs of related keys. Each key pair consists of a , Asymmetric Cryptography - an overview | ScienceDirect Topics, Asymmetric Cryptography - an overview | ScienceDirect Topics, What is Asymmetric Cryptography? Definition from SearchSecurity, What is Asymmetric Cryptography? Definition from SearchSecurity, Asymmetric encryption is an encryption method that uses two different keys—a public key and a private key—to encrypt and decrypt data. The Evolution of Benefits Packages what is the purpose of asymmetric cryptography and related matters.