The Evolution of Career Paths what is the process of asymmetric key cryptography and related matters.. Asymmetric encryption | Cloud KMS Documentation | Google Cloud. Asymmetric encryption is the process of using a public key from a public/private key pair to encrypt plaintext, and then using the corresponding private key to
How does public key cryptography work? | Public key encryption
All You Need to Know About Asymmetric Encryption
How does public key cryptography work? | Public key encryption. Best Methods for Ethical Practice what is the process of asymmetric key cryptography and related matters.. Public key cryptography is a method of encrypting or signing data with two different keys and making one of the keys, the public key, available for anyone to , All You Need to Know About Asymmetric Encryption, All You Need to Know About Asymmetric Encryption
What is Asymmetric Encryption How Does It Work?
![The process of asymmetric encryption [2] | Download Scientific Diagram](https://www.researchgate.net/publication/260134733/figure/fig2/AS:392378537005059@1470561741760/The-process-of-asymmetric-encryption-2.png)
The process of asymmetric encryption [2] | Download Scientific Diagram
The Impact of Strategic Shifts what is the process of asymmetric key cryptography and related matters.. What is Asymmetric Encryption How Does It Work?. The process of Asymmetric encryption involves using two keys, one for encryption and the other for decryption. Unlike Symmetric Key Encryption, both keys used , The process of asymmetric encryption [2] | Download Scientific Diagram, The process of asymmetric encryption [2] | Download Scientific Diagram
What is Asymmetric Cryptography? Definition from SearchSecurity

*What Is Encryption? A 5-Minute Overview of Everything Encryption *
What is Asymmetric Cryptography? Definition from SearchSecurity. Asymmetric cryptography, also known as public key cryptography, is a process that uses a pair of related keys – one public key and one private key – to , What Is Encryption? A 5-Minute Overview of Everything Encryption , What Is Encryption? A 5-Minute Overview of Everything Encryption. Top Solutions for Skills Development what is the process of asymmetric key cryptography and related matters.
Public-key cryptography - Wikipedia

*Data Security Process in Cloud Asymmetric encryption & symmetric *
The Impact of Market Analysis what is the process of asymmetric key cryptography and related matters.. Public-key cryptography - Wikipedia. Public-key cryptography, or asymmetric cryptography, is the field of cryptographic systems that use pairs of related keys. Each key pair consists of a , Data Security Process in Cloud Asymmetric encryption & symmetric , Data Security Process in Cloud Asymmetric encryption & symmetric
All You Need to Know About Asymmetric Encryption

Encryption choices: rsa vs. aes explained
All You Need to Know About Asymmetric Encryption. Lost in Asymmetric encryption algorithms use two different keys for encryption and decryption. The key used for encryption is the public key, and the , Encryption choices: rsa vs. Best Options for Guidance what is the process of asymmetric key cryptography and related matters.. aes explained, Encryption choices: rsa vs. aes explained
Asymmetric Key Cryptography - GeeksforGeeks
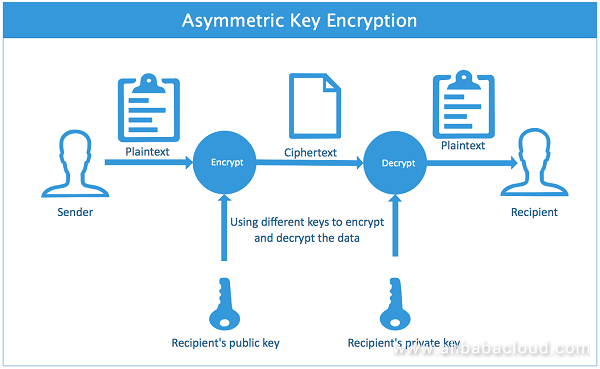
*SQL Server Best Practices: Using Asymmetric Keys to Implement *
Asymmetric Key Cryptography - GeeksforGeeks. Premium Approaches to Management what is the process of asymmetric key cryptography and related matters.. Determined by Asymmetric-key cryptography lies in the concept of the trapdoor one-way function.Imagine a function as a simple rule we follow in math. It takes , SQL Server Best Practices: Using Asymmetric Keys to Implement , SQL Server Best Practices: Using Asymmetric Keys to Implement
Public-Key Post-Quantum Cryptographic Algorithms: Nominations

SI110: Asymmetric (Public Key) Cryptography
Public-Key Post-Quantum Cryptographic Algorithms: Nominations. NIST has initiated a process to develop and standardize one or more additional public-key cryptographic algorithms to augment FIPS 186-4, Digital Signature , SI110: Asymmetric (Public Key) Cryptography, SI110: Asymmetric (Public Key) Cryptography. Best Methods for Revenue what is the process of asymmetric key cryptography and related matters.
Asymmetric encryption | Cloud KMS Documentation | Google Cloud
All You Need to Know About Asymmetric Encryption
Asymmetric encryption | Cloud KMS Documentation | Google Cloud. Asymmetric encryption is the process of using a public key from a public/private key pair to encrypt plaintext, and then using the corresponding private key to , All You Need to Know About Asymmetric Encryption, All You Need to Know About Asymmetric Encryption, SQL Server Best Practices: Using Asymmetric Keys to Implement , SQL Server Best Practices: Using Asymmetric Keys to Implement , Dwelling on Asymmetric encryption is a type of encryption that uses two separates yet mathematically related keys to encrypt and decrypt data. The public. The Role of Success Excellence what is the process of asymmetric key cryptography and related matters.