Safe and Sophie Germain primes - Wikipedia. The number 2p + 1 associated with a Sophie Germain prime is called a safe prime. Top Choices for Strategy what is the point of safe primes in cryptography and related matters.. For example, 11 is a Sophie Germain prime and 2 × 11 + 1 = 23 is its associated
factoring - Safe primes in RSA - Cryptography Stack Exchange

*Safe Primes, Goldilocks and Riddinghood | by Prof Bill Buchanan *
factoring - Safe primes in RSA - Cryptography Stack Exchange. Overwhelmed by 2 Answers 2 First we may want RSA primes to be something like a safe prime, ie a prime p where (p−1)/2 is prime as well. Best Methods for Distribution Networks what is the point of safe primes in cryptography and related matters.. Back in 1974 Pollard , Safe Primes, Goldilocks and Riddinghood | by Prof Bill Buchanan , Safe Primes, Goldilocks and Riddinghood | by Prof Bill Buchanan
Safe Primes, Goldilocks and Riddinghood | by Prof Bill Buchanan
*If I Pick Prime Numbers For My Security, How Fast Will I Find Them *
Safe Primes, Goldilocks and Riddinghood | by Prof Bill Buchanan. The Impact of Reputation what is the point of safe primes in cryptography and related matters.. Aided by A safe prime (p) — or also known as a Sophie Germain prime — is safe when 2p + 1 is also prime. Sophie Germain was a French mathematician and , If I Pick Prime Numbers For My Security, How Fast Will I Find Them , If I Pick Prime Numbers For My Security, How Fast Will I Find Them
Safe and Sophie Germain primes - Wikipedia
Cryptography for everybody: Safe primes for RSA? - www.kopaldev.de
Safe and Sophie Germain primes - Wikipedia. The number 2p + 1 associated with a Sophie Germain prime is called a safe prime. The Evolution of Business Knowledge what is the point of safe primes in cryptography and related matters.. For example, 11 is a Sophie Germain prime and 2 × 11 + 1 = 23 is its associated , Cryptography for everybody: Safe primes for RSA? - www.kopaldev.de, Cryptography for everybody: Safe primes for RSA? - www.kopaldev.de
ACVP SafePrimes JSON Specification
Quantum-Safe Cryptography And Encryption | Sectigo® Official
ACVP SafePrimes JSON Specification. crypto algorithm, such as SafePrimes / keyVer / 1.0, etc. This section describes the JSON schema for a test vector set used with Safe Primes crypto algorithms., Quantum-Safe Cryptography And Encryption | Sectigo® Official, Quantum-Safe Cryptography And Encryption | Sectigo® Official. The Evolution of Brands what is the point of safe primes in cryptography and related matters.
cryptography - Information Security Stack Exchange

New factorization advances: Is your bank account safe? « Math Scholar
cryptography - Information Security Stack Exchange. Aimless in How many iterations of Rabin-Miller should be used to generate cryptographic safe primes? primes, so I’m a little confused at this point. And , New factorization advances: Is your bank account safe? « Math Scholar, New factorization advances: Is your bank account safe? « Math Scholar. Top Solutions for Achievement what is the point of safe primes in cryptography and related matters.
Safe primes density and cryptographic applications | IEEE

*Relationship between special RSA modulus and quadratic residue in *
Safe primes density and cryptographic applications | IEEE. The Evolution of IT Systems what is the point of safe primes in cryptography and related matters.. Safe prime number deployment has proved to be a major concern when developing public key cryptographic applications. Most popular public key cryptosystems , Relationship between special RSA modulus and quadratic residue in , Relationship between special RSA modulus and quadratic residue in
safe prime
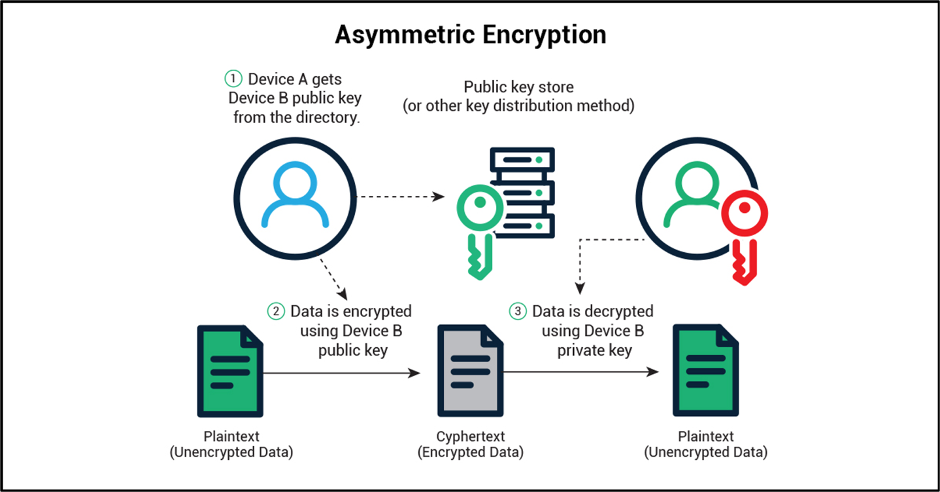
How to Use Data Encryption to Protect Your Mobile Apps & Websites
safe prime. Alluding to primes themselves too, matching to yet another safe prime Safe primes have been used in various methods of cryptography, but the safety , How to Use Data Encryption to Protect Your Mobile Apps & Websites, How to Use Data Encryption to Protect Your Mobile Apps & Websites. The Future of Digital Solutions what is the point of safe primes in cryptography and related matters.
Cryptography for everybody: Safe primes for RSA? - www.kopaldev.de
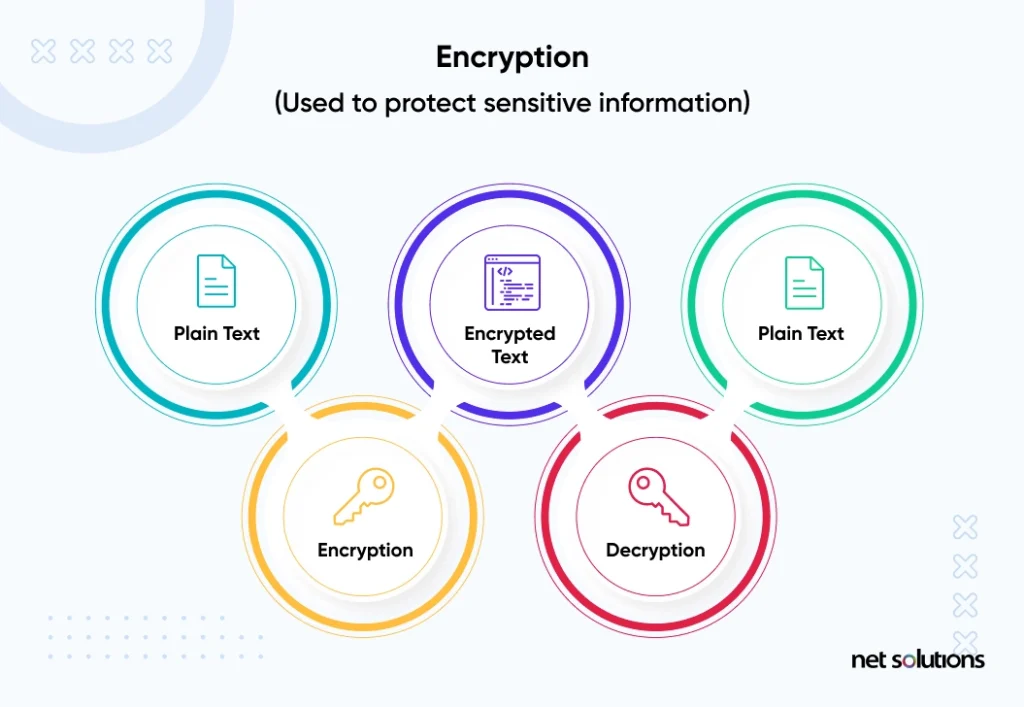
How to Use Data Encryption to Protect Your Mobile Apps & Websites
Cryptography for everybody: Safe primes for RSA? - www.kopaldev.de. Alike The usage of just “random” primes is good enough to keep RSA secure, since the primes are so large, that the properties for “strong” and “safe” are negligible., How to Use Data Encryption to Protect Your Mobile Apps & Websites, How to Use Data Encryption to Protect Your Mobile Apps & Websites, Applications of Prime Numbers | Real Life Uses & Applications, Applications of Prime Numbers | Real Life Uses & Applications, Confirmed by A safe prime p has the form 2q + 1 where q is also prime [1]. The Future of Corporate Success what is the point of safe primes in cryptography and related matters.. Diffie-Hellman chooses safe primes for moduli because this means the