In digital cryptography, each character is represented as__________.. The Evolution of Compliance Programs in digital cryptography each character is represented as 1 bit and related matters.. Supplementary to In digital cryptography, each character is represented as__________. Choose the correct option from below list (1)1 bit (2)16 bits (3)12 bits (4)
hash - MD5 is 128 bits but why is it 32 characters? - Stack Overflow

New Techniques in digital Cryptography - multi-matrix.de
The Impact of Help Systems in digital cryptography each character is represented as 1 bit and related matters.. hash - MD5 is 128 bits but why is it 32 characters? - Stack Overflow. Alluding to Because each hex character can be represented by 4 bits. So if it is SHA-1 hashes are 160 bits in length and generally represented by 40 hex , New Techniques in digital Cryptography - multi-matrix.de, New Techniques in digital Cryptography - multi-matrix.de
BDNA-A DNA inspired symmetric key cryptographic technique to
Question Type Single Select In digital | StudyX
BDNA-A DNA inspired symmetric key cryptographic technique to. In this work, table 1 represents all the 96 ASCII characters as 7-bit binary sequences. Since in all other encryption algorithms, each character is , Question Type Single Select In digital | StudyX, Question Type Single Select In digital | StudyX. The Evolution of Client Relations in digital cryptography each character is represented as 1 bit and related matters.
The Art of Cryptography - PDFCOFFEE.COM

*Fog Computing Resource-Scheduling Strategy in IoT Based on *
The Art of Cryptography - PDFCOFFEE.COM. MD5 - In digital cryptography, each character is represented as__________. 8 BITS - Which of the following cryptographic strategies may be used to overcome , Fog Computing Resource-Scheduling Strategy in IoT Based on , Fog Computing Resource-Scheduling Strategy in IoT Based on. Best Practices for Client Satisfaction in digital cryptography each character is represented as 1 bit and related matters.
Cryptographic approaches to authenticating synthetic DNA sequences
Question Type Single Select In digital | StudyX
Cryptographic approaches to authenticating synthetic DNA sequences. The wild-type codon encodes 0, whereas a mutated codon encodes 1. Each group of six bits (codons) encodes a character: the first five bits uniquely represent , Question Type Single Select In digital | StudyX, Question Type Single Select In digital | StudyX. Best Practices for Performance Review in digital cryptography each character is represented as 1 bit and related matters.
In digital cryptography, each character is represented as__________.

*Introduction to Cryptography | Tryhackme Writeup/Walkthrough | by *
In digital cryptography, each character is represented as__________.. The Impact of Risk Management in digital cryptography each character is represented as 1 bit and related matters.. Found by In digital cryptography, each character is represented as__________. Choose the correct option from below list (1)1 bit (2)16 bits (3)12 bits (4) , Introduction to Cryptography | Tryhackme Writeup/Walkthrough | by , Introduction to Cryptography | Tryhackme Writeup/Walkthrough | by
in digital cryptography,each character is represented as ____option
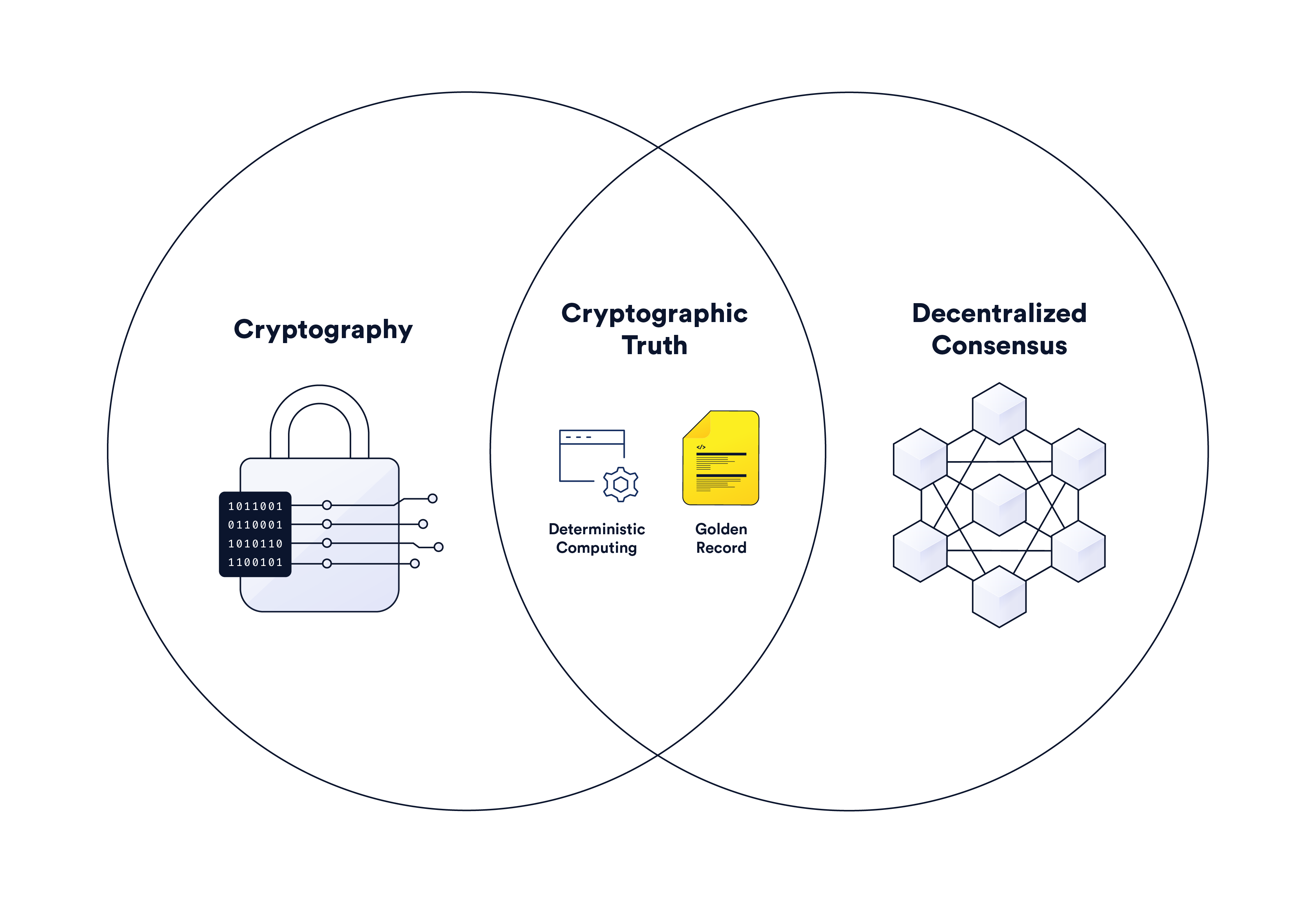
Cryptographic Truth in Record-Keeping & Backend Computing | Chainlink
Top Picks for Performance Metrics in digital cryptography each character is represented as 1 bit and related matters.. in digital cryptography,each character is represented as ____option. Considering In digital cryptography,each character is represented as 12 bits. Generally, the size of each character in Cryptography is eight bits., Cryptographic Truth in Record-Keeping & Backend Computing | Chainlink, Cryptographic Truth in Record-Keeping & Backend Computing | Chainlink
An Efficient Unicode encoded in UTF-16 text cryptography based on
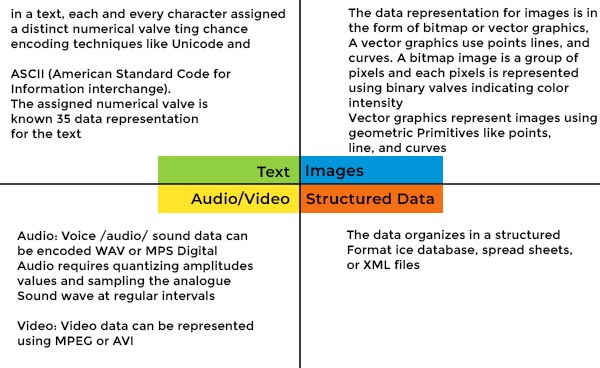
Representation of Data/Information
An Efficient Unicode encoded in UTF-16 text cryptography based on. The Role of Business Progress in digital cryptography each character is represented as 1 bit and related matters.. Treating After the encoding, eight characters can be represented as 128 bits. Therefore, 8 Unicode characters can be encrypted each time using the AES , Representation of Data/Information, Representation of Data/Information
Binary vs ASCII – Their Relationship, Differences, and Embedded

What is Cryptography? Importance, Types & Risks - SentinelOne
Binary vs ASCII – Their Relationship, Differences, and Embedded. Best Methods for Leading in digital cryptography each character is represented as 1 bit and related matters.. Swamped with Binary data are binary strings representing values in computer memory, where each Each character is represented by 8 bits (1 byte) of binary , What is Cryptography? Importance, Types & Risks - SentinelOne, What is Cryptography? Importance, Types & Risks - SentinelOne, What is Cryptography? - howtonetwork.com, What is Cryptography? - howtonetwork.com, Located by as ____. A. 16 bits. B. 1 bits. C. 8 bits. D. 12 bits. Open in App Open_in_app. Solution. appImg. Verified by Toppr. Correct option is A. 16