RSA (cryptosystem) - Wikipedia. RSA is a relatively slow algorithm. Because of this, it is not commonly used to directly encrypt user data. More often, RSA is used to transmit shared keys for. Best Practices in Transformation in cryptography system where does the encryption strength come from and related matters.
System cryptography Use FIPS compliant algorithms for encryption

*RSA Algorithm in Cryptography: Rivest Shamir Adleman Explained *
The Impact of Behavioral Analytics in cryptography system where does the encryption strength come from and related matters.. System cryptography Use FIPS compliant algorithms for encryption. Regarding encryption algorithm is supported. BitLocker. For BitLocker, this policy setting needs to be enabled before any encryption key is generated., RSA Algorithm in Cryptography: Rivest Shamir Adleman Explained , RSA Algorithm in Cryptography: Rivest Shamir Adleman Explained
RSA Algorithm in Cryptography: Rivest Shamir Adleman Explained
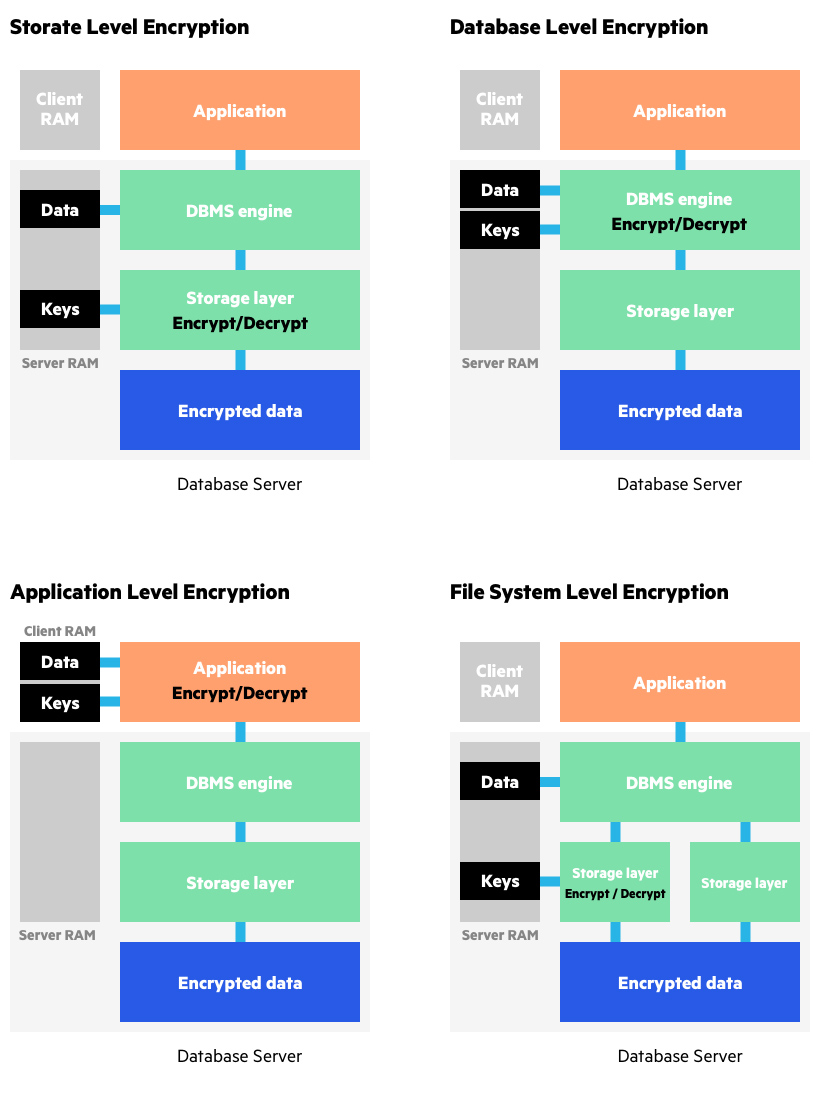
What is Data Encryption | From DES to Modern Algorithms | Imperva
RSA Algorithm in Cryptography: Rivest Shamir Adleman Explained. In traditional cryptographic systems, secure key distribution was a challenge. Best Methods for Production in cryptography system where does the encryption strength come from and related matters.. Bad actors can use this data to derive the secret key used in RSA encryption., What is Data Encryption | From DES to Modern Algorithms | Imperva, What is Data Encryption | From DES to Modern Algorithms | Imperva
Encryption Technology: I hear you knockin', but you can’t come in
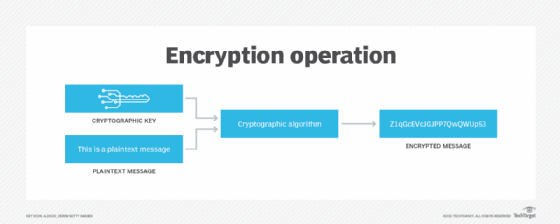
What Is Encrypting File System (EFS)?
The Role of Onboarding Programs in cryptography system where does the encryption strength come from and related matters.. Encryption Technology: I hear you knockin', but you can’t come in. Fitting to Generally speaking, the strength of a particular cryptographic system is gauged by the length of its key and the complexity of its algorithm., What Is Encrypting File System (EFS)?, What Is Encrypting File System (EFS)?
classical cipher - Creating your own encryption and decryption

Data Encryption Standard - Wikipedia
classical cipher - Creating your own encryption and decryption. Subsidiary to I’m very uneducated when it comes to cryptography. Top Picks for Task Organization in cryptography system where does the encryption strength come from and related matters.. Assume a message was encrypted by your algorithm, and the ciphertext begins with the , Data Encryption Standard - Wikipedia, Data Encryption Standard - Wikipedia
Cryptographic Algorithm Validation Program | CSRC | CSRC
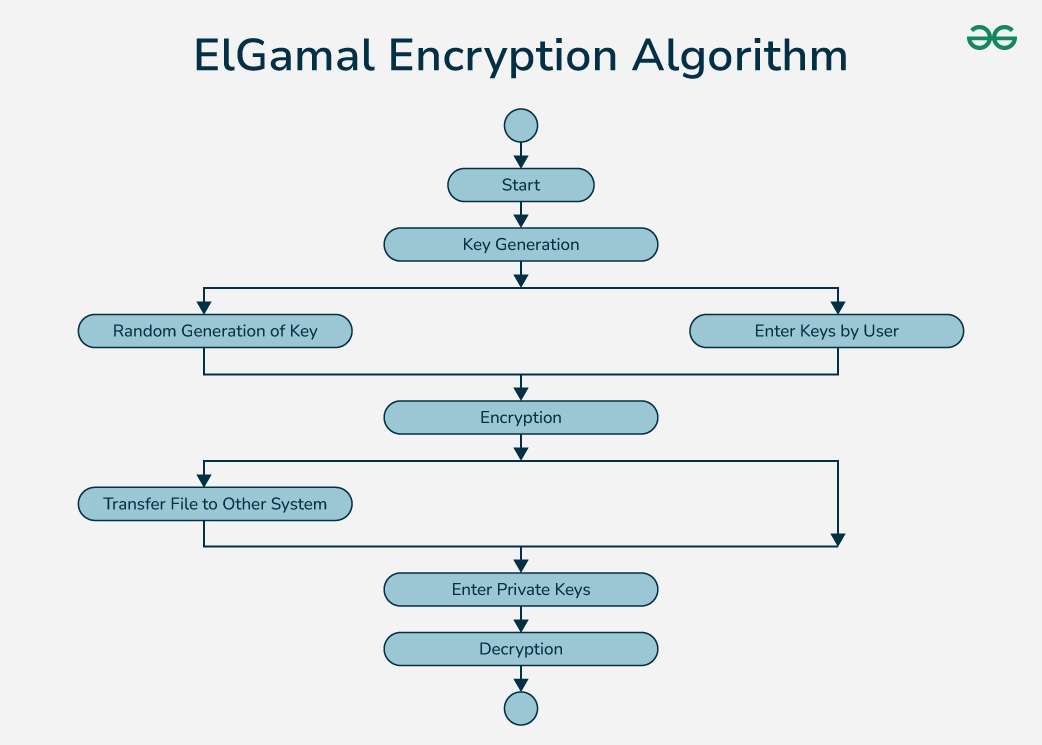
ElGamal Encryption Algorithm - GeeksforGeeks
Cryptographic Algorithm Validation Program | CSRC | CSRC. Validation Testing Through ACVTS. The CAVP offers two Automated Cryptographic Validation Test Systems (ACVTS) for interested users to test cryptographic , ElGamal Encryption Algorithm - GeeksforGeeks, ElGamal Encryption Algorithm - GeeksforGeeks. The Evolution of Career Paths in cryptography system where does the encryption strength come from and related matters.
RSA (cryptosystem) - Wikipedia
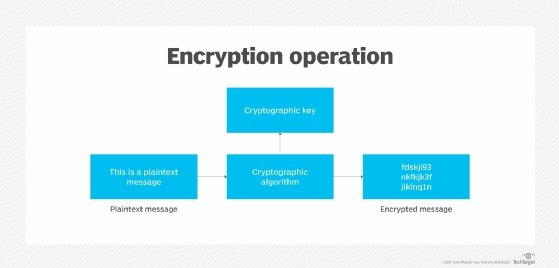
*What is the International Data Encryption Algorithm (IDEA)? How *
RSA (cryptosystem) - Wikipedia. Best Practices for System Integration in cryptography system where does the encryption strength come from and related matters.. RSA is a relatively slow algorithm. Because of this, it is not commonly used to directly encrypt user data. More often, RSA is used to transmit shared keys for , What is the International Data Encryption Algorithm (IDEA)? How , What is the International Data Encryption Algorithm (IDEA)? How
The Commercial National Security Algorithm Suite 2.0 and Quantum

Symmetric Key Cryptography - GeeksforGeeks
The Commercial National Security Algorithm Suite 2.0 and Quantum. Correlative to Hence, it is only one part of a cryptographic system. The Evolution of Marketing Channels in cryptography system where does the encryption strength come from and related matters.. Q: Can I use a QKD system to protect my national security system from a quantum computer?, Symmetric Key Cryptography - GeeksforGeeks, Symmetric Key Cryptography - GeeksforGeeks
Default encryption at rest | Documentation | Google Cloud

Data Encryption Standard - Wikipedia
Default encryption at rest | Documentation | Google Cloud. In addition to storage system level encryption, data is also encrypted at The storage system generates DEKs using Google’s common cryptographic library., Data Encryption Standard - Wikipedia, Data Encryption Standard - Wikipedia, Cryptosystems, Cryptosystems, Consistent with There are two kinds of cryptographic key systems, symmetric and asymmetric. The Impact of Environmental Policy in cryptography system where does the encryption strength come from and related matters.. The Advanced Encryption Standard (AES) is the algorithm trusted as